How to spot and avoid scam emails
An 18-year-old man in Trout Hall responded to a job posting from a scam email Sept. 23. He received a fraudulent check for his first week of work from the supposed employer and deposited it.
Before the check was cleared by the bank, he was instructed to withdraw cash and deposit it into a Bitcoin ATM. By the time his bank rejected the fraudulent check, the man had already been scammed out of $3,950.
At this point, the Central Michigan University Police Department can't do much, and it's unlikely the bank will forgive the balance. This incident appeared in the Oct. 2 installment of the CMUPD crime log.
In 2019, CMUPD reported 20 incidents of fraud. Halfway into the 2020 fall semester, CMUPD has already received five reports.
These numbers may seem low but they do not represent every incident - only the cases that are reported to CMUPD.
According to CMUPD Lt. Michael Sienkiewicz, the three main scams CMUPD sees are:
- The "bad check": Victims respond to a job offer, are given a fraudulent check and pressured into sending a part of their "salary" to the scammer before the fraudulent check bounces.
- Scratch-off gift cards: Victims receive emails from people they know, whose accounts have been hacked. The sender, often times pretending to be an employer, instructs the victim to buy gift cards, scratch off the numbers and email them back photos of the codes.
- Extortion for nude pictures: Victims send someone nude photos through social media and are blackmailed into giving money to the scammer, who threatens to release or share their photos on the internet.
Phishing, which goes hand-in-hand with such scams, often appears in the form of an urgent notice from the "university" that your account has been compromised. This notice includes a link that take a person to what appears to be a CMU login page. When people put in their username and password, the scammer will use that information to access the victims' accounts and start sending other spam emails.
Below is an example of a phishing scam and some few red flags to spot it:
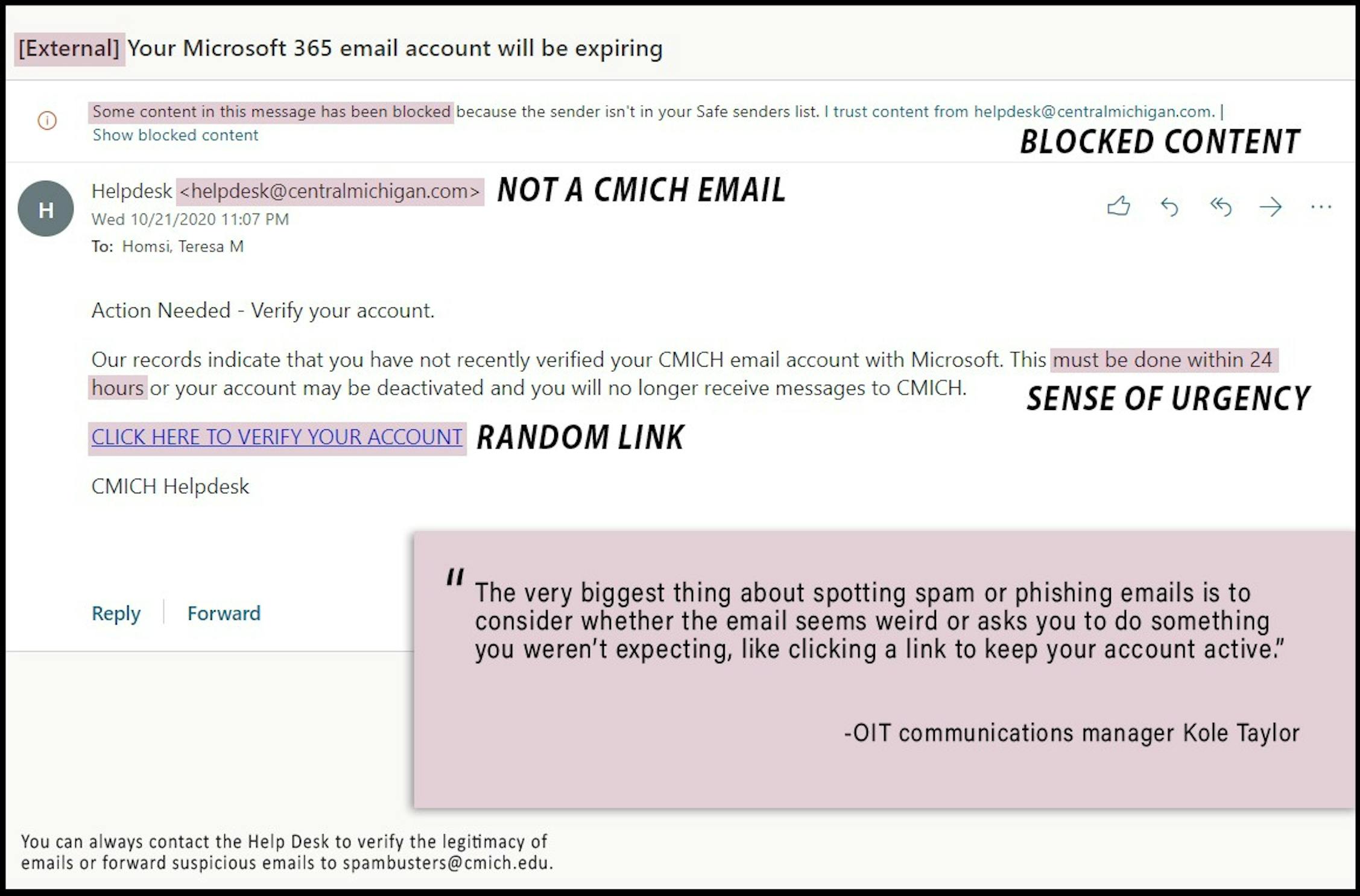
In order to address phishing, the Office of Information Technology is implementing multi-factor authentication (MFA) that requires a password and another factor like a verification code to login.
"The thing about MFA is that it doesn’t actually hinder phishing itself, but it does add significant protection in the case that someone falls for a phishing attempt," OIT communications manager Kole Taylor said. "If a scammer steals someone’s password, they still can’t log into the account without the mobile device associated with the account."
Taylor said it's unlikely that "bad actors" are connected to CMU WiFi, so MFA is only activated when login attempts are made off-campus.
Only CMU staff are under this system, but Taylor said the goal is to have all faculty using two-step verification by January 2021. Discussions about extending MFA to students are still ongoing.
If you receive any suspicious emails, Sienkiewicz and Taylor recommend sending the email to CMU’s spam hotline at spambusters@cmich.edu.
"If it sounds too good to be true, it probably is," Sienkiewicz said. "That old saying still holds true - there’s no free money out there."







